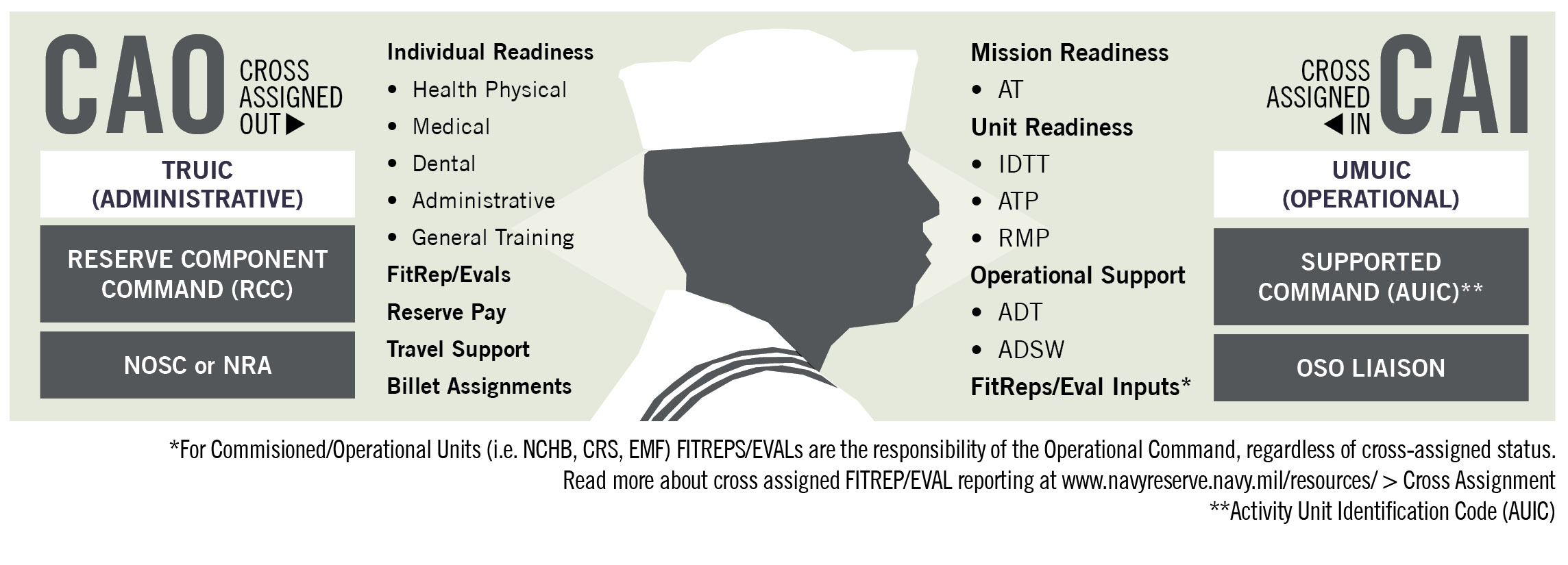
which of the following are breach prevention best practices jko
All of the above An incidental use or disclosure is not a violation of the HIPAA Privacy Rule if the covered entity. Identify areas that store transmit collect or process.
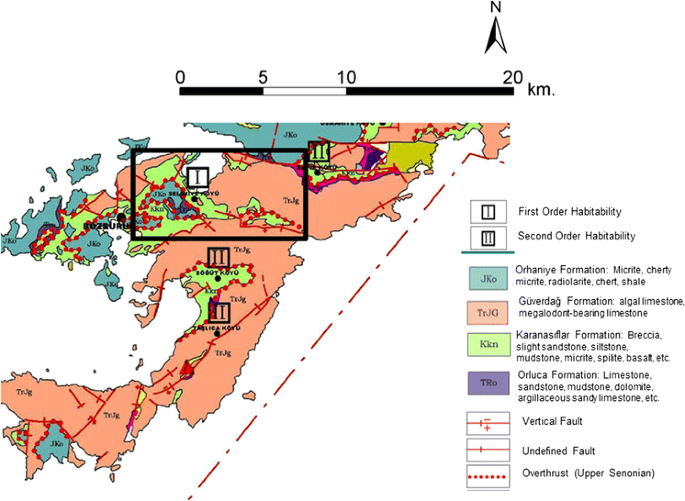
Searching Ancient Territorium Of Hygassos In Anatolia Settlement Patterns And Spatio Temporal Investigations Through Aerial And Gis Applications Springerlink
Which of the following are breach prevention best practices.
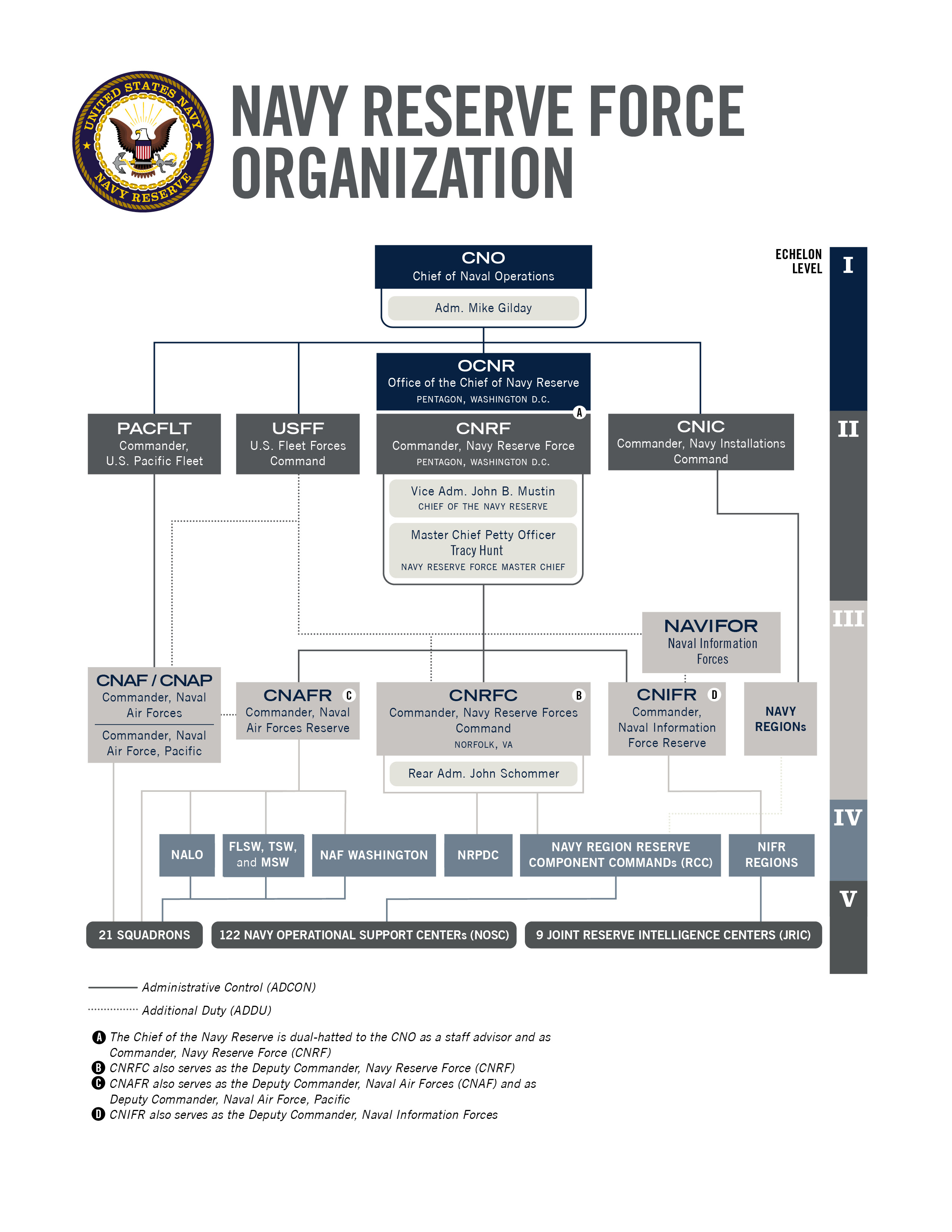
. All of the above An incidental use or disclosure is not a violation of the HIPAA Privacy Rule if the covered entity. Ad In The Professional Liability Arena We Provide State-Of-The-Art Coverage For Cyber Risks. A balances the privacy rights of individuals with the governments need to collect and maintain information.
Which of the following are breach prevention best practices. Identity sensitive data collected stored transmitted or processes. Which of the following are breach prevention best practices.
The employees play an essential responsibility in keeping their. HIPAA and Privacy Act Training 15 hrs DHA-US001 4. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your.
JKO HIPAA and Privacy Act Training 15 hrs 2. Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your. Focusing on the security measures of your company is very important.
Which of the following are breach. Which of the following are breach prevention best practices. 5 a breach of these obligations or restrictions may subject the contractor to.
Beazley Provides A Full Range Of Resources To Help Mitigate Cyber Risk. Which of the following are breach prevention best practices. 30 Best Practices for Preventing a Data Breach.
Which of the following are breach prevention best practices. In the age of digital data keeping information safe is more important than ever. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary andby promptly.
Developing the IRP will help the IT staff of the company to control the data breach incidents. Which of the following are breach prevention best practices. HIPAA and Privacy Act Training 2022 WITH COMPLETE SOLUTIONS 3.
Train Employees on Security Awareness. Which of the following are breach prevention best practices.

Which Of The Following Are Breach Prevention Best Practices Public Health

Hipaa And Privacy Act Challenge Exam Docx Hipaa And Privacy Act Training Challenge Exam Joint Knowledge Online Jko Dha Us001 Select Your Current Course Hero
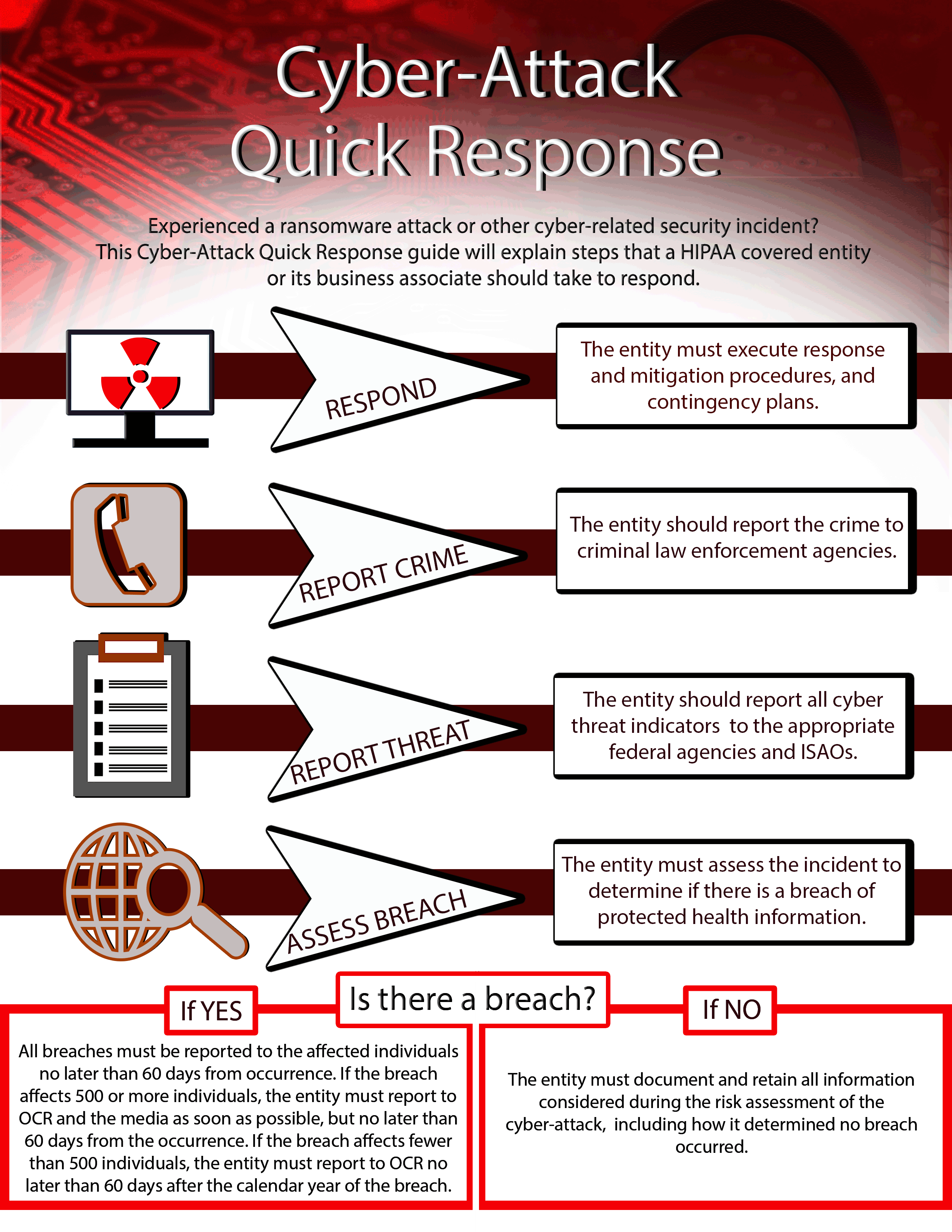
Cyber Security Guidance Material Hhs Gov

Opnavinst5100 19f Pdf Safety Nature

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

Which Of The Following Are Breach Prevention Best Practices Public Health

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Which Of The Following Are Breach Prevention Best Practices Public Health

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero
Hipaa Jko Remedial Flashcards Quizlet

Hipaa And Privacy Act Challenge Exam Docx Hipaa And Privacy Act Training Challenge Exam Joint Knowledge Online Jko Dha Us001 Select Your Current Course Hero

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

Good%20Year%20graphic.jpg?ver=aw99W3KoI9CzYK-tSAvkkw%3D%3D)